For more than five years, DC/OS has enabled some of the largest, most sophisticated enterprises in the world to achieve unparalleled levels of efficiency, reliability, and scalability from their IT infrastructure. But now it is time to pass the torch to a new generation of technology: the D2iQ Kubernetes Platform (DKP). Why? Kubernetes has now achieved a level of capability that only DC/OS could formerly provide and is now evolving and improving far faster (as is true of its supporting ecosystem). That’s why we have chosen to sunset DC/OS, with an end-of-life date of October 31, 2021. With DKP, our customers get the same benefits provided by DC/OS and more, as well as access to the most impressive pace of innovation the technology world has ever seen. This was not an easy decision to make, but we are dedicated to enabling our customers to accelerate their digital transformations, so they can increase the velocity and responsiveness of their organizations to an ever-more challenging future. And the best way to do that right now is with DKP.

We are proud to announce the general availability of DC/OS 2.1, which includes new enterprise-grade capabilities across the following key areas:
- Cluster Utilization
- Virtual Networking
- Enterprise Security
These new capabilities further enhance the standing of DC/OS as the most robust, scalable cloud native platform for enterprises.
Highlights of DC/OS 2.1
Cluster Utilization
Vertical Container Bursting
DC/OS now enables you to set a limit on the amount of CPUs or memory used by a Marathon app/pod that is different from the requested amount of CPUs or memory. This feature guarantees a minimum amount of resources to a container (request), while allowing it to burst up to the limit if there are sufficient resources available on the node.
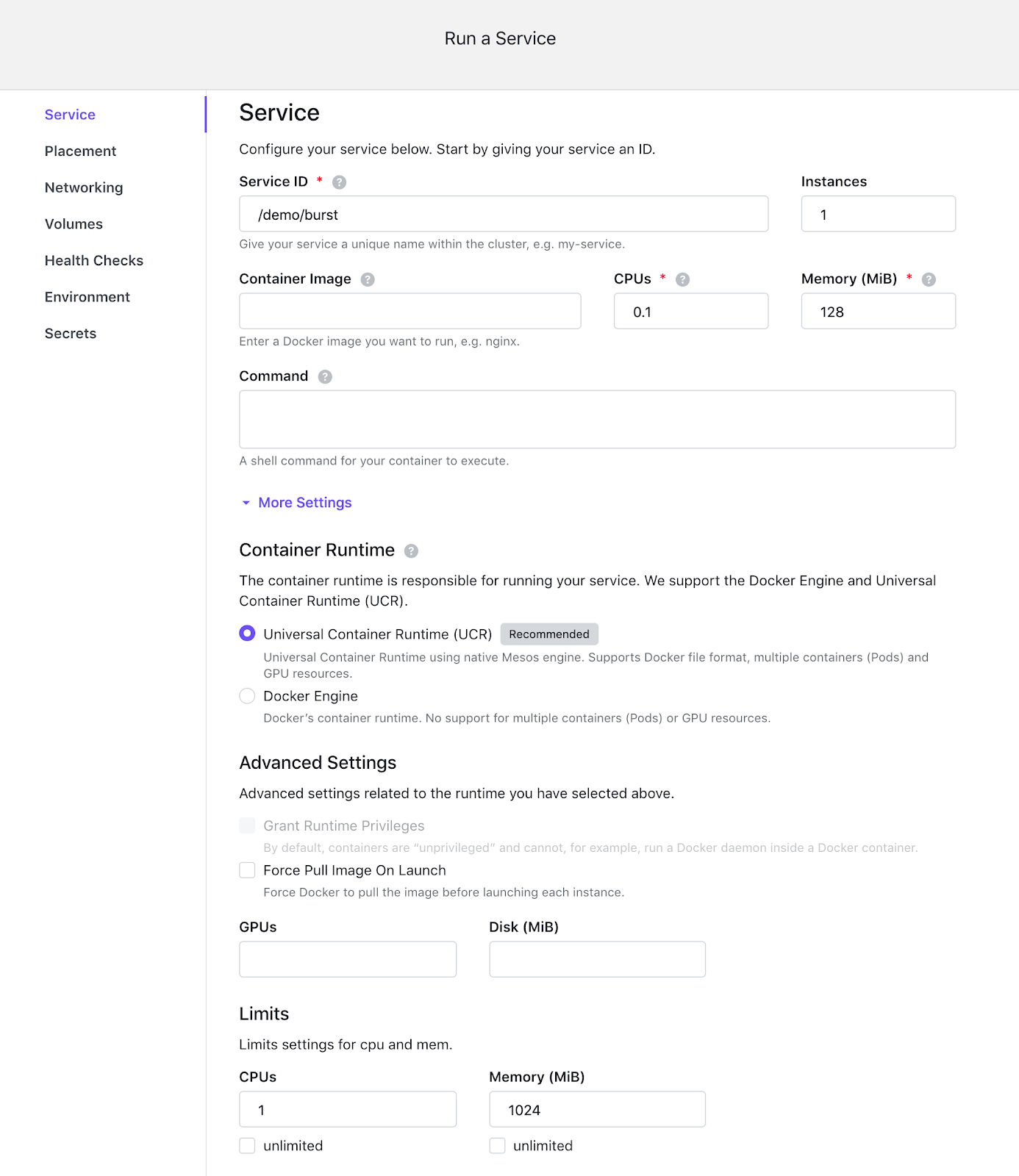
This feature is particularly useful for those applications that have different resource usage patterns over their lifetime. For example, JVM based applications typically use a large amount of memory during startup, compared to their steady state. Most web applications’ resource usage changes based on the volume of user traffic that they are handling. Previously, provisions had to be resourced for these applications based on their peak usage, resulting in under-utilization of cluster resources. With the vertical bursting feature, you can now set the resource requests of an application to match the steady state usage and set limits to account for peaks. See Creating a Service in the DC/OS help for more information.
Virtual Networking
Network Policies with Calico
Calico is now pre-installed with DC/OS 2.1 and is an alternative SDN solution to the DC/OS Overlay. The DC/OS Calico component integrates Calico networking into DC/OS, providing the Calico CNI plug-in for Mesos Universal Container Runtime and the Calico libnetwork plug-in for Docker Engine.
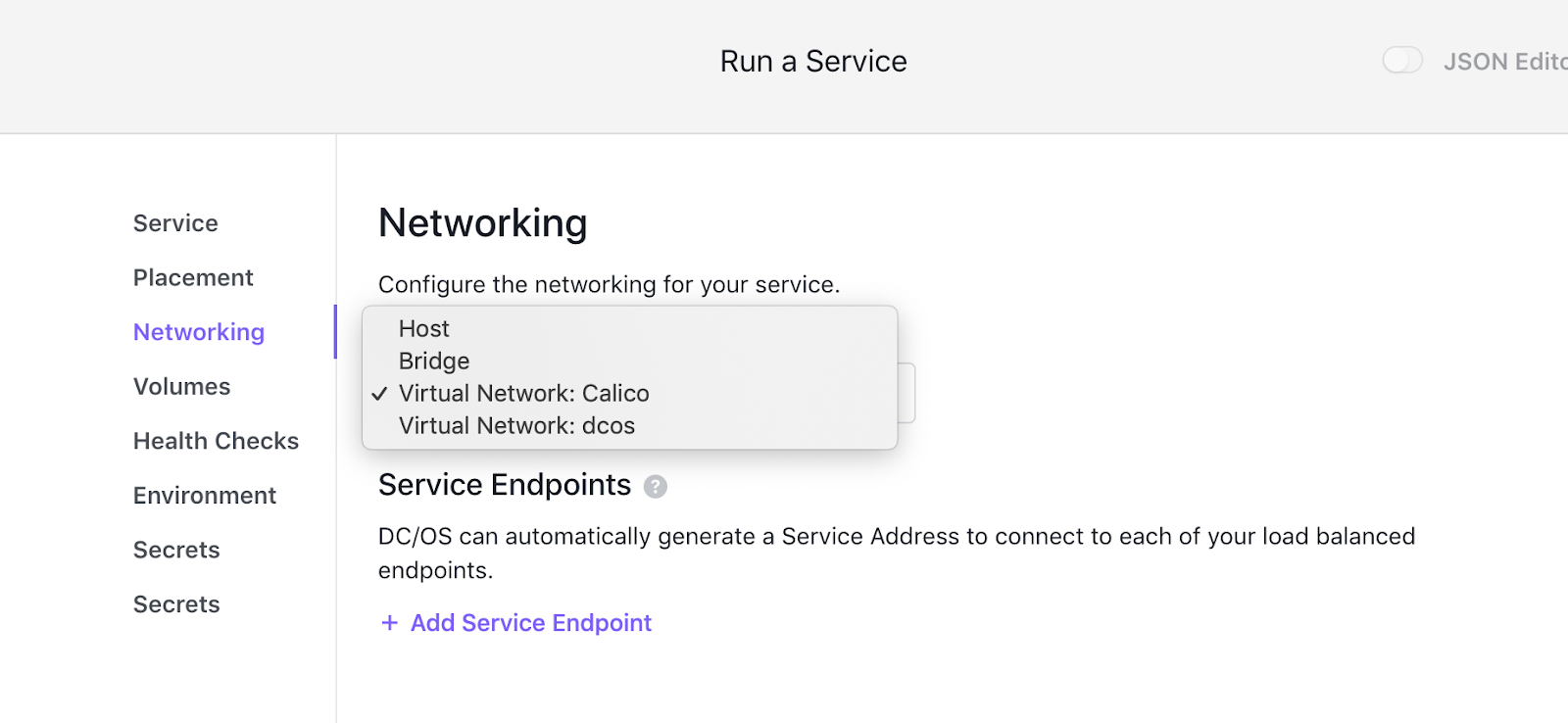
One of the advantages of using Calico as the virtual networking provider is the ability to set network policies. Network policies provide the ability to control network traffic by an ordered set of rules applied to the endpoints specified by a label selector. In DC/OS, a Calico network policy is exposed directly to the operators, so that the operator can manage their traffic control according to different scenarios. See Understanding Calico in the DC/OS help for more information.
Jobs Virtual Networking Support
Metronome-based jobs can now join container networks, to communicate with other services/jobs in the same network.
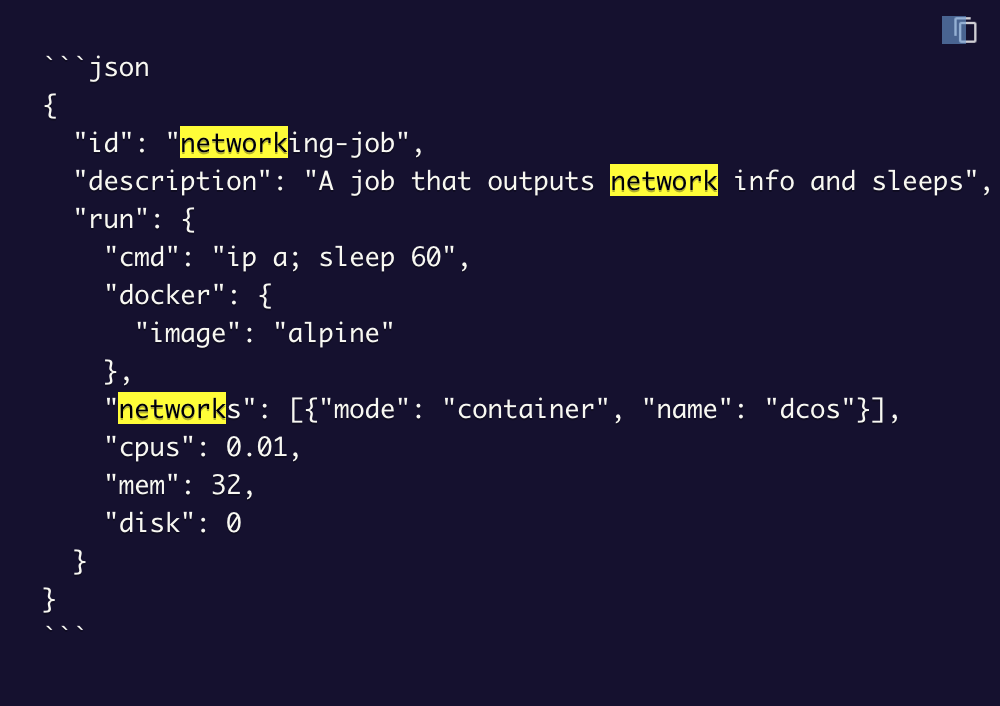
The Metronome Networks function is identical to Marathon's Networks function and supports the following parameters:
- mode: The network mode. Valid values are `container`, `container/bridge` and `host`. The default value is `host`.
- name: The name of the container network to join.
- labels: Key-value string arguments to pass to the networking plug-in.
See Creating Jobs in the DC/OS help for more information.
Enterprise Security
Custom External Certificates for Admin Router
This feature allows operators to provide a custom non-CA certificate that is then used by Admin Router for external clients connecting to a cluster. By default, the certificate presented by Admin Router is signed by the DC/OS Certificate Authority. The default DC/OS CA certificate is not trusted by default, and requires clients to manually configure trust in the CA (e.g. by accepting a pop-up browser dialog). A trusted CA certificate can be provided using custom CA certificates. However, obtaining a suitable CA certificate can be difficult. Custom external certificates allow the cluster administrator to provide an easily obtained non-CA certificate and key that Admin Router will present to external connections.
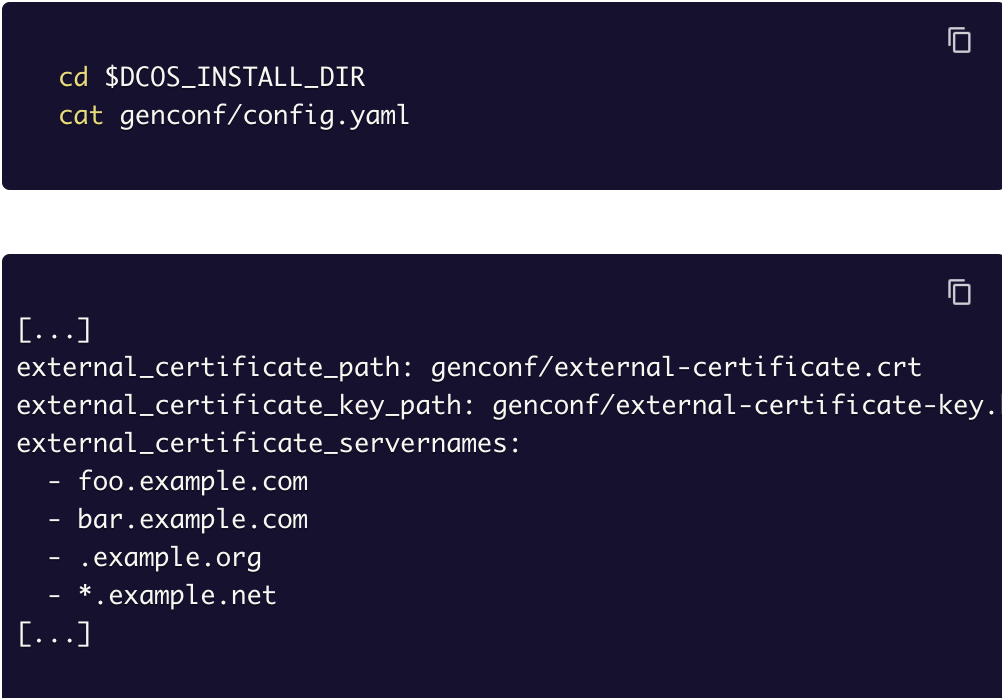
The benefits of using a custom external certificate for your DC/OS Enterprise cluster include:
- Only needing to obtain a standard certificate instead of an intermediate CA signing certificate to make connections to the cluster trusted by the clients by default (i.e. browser-trusted certificates)
- Using a certificate with different properties for clients connecting to the cluster using different server names.
See Configuring a Custom Certificate in the DC/OS help for more information.
What we have shown above is just a glimpse of the new features that are in DC/OS 2.1. For more detailed information about everything in the release, refer to the DC/OS 2.1 Release Notes.
For those who may be interested in learning more about DC/OS Enterprise, please contact us and we will be glad to assist you.