Update
We are very pleased to announce that we have received Federal Information Processing Standards (FIPS) Validation (CMVP Cert #3702) for the D2iQ Kubernetes Platform (DKP). With FIPS validation, U.S. public sector organizations can accelerate adoption of the D2iQ Kubernetes Platform to more quickly and securely build and deploy cloud native applications and services.
What is FIPS and Why Should I Care?
Many government agencies in the United States require Federal Information Processing Standards (FIPS) compliance or validation for deployed software. D2iQ works with many U.S. government agencies and has a history of delivering FIPS compliant platforms as part of these partnerships. The new Kubernetes and Cloud Native ecosystem-based D2iQ Kubernetes Platform products are no different and have now received FIPS validation.
Security Background
The main objective of cybersecurity is to protect “information assets by addressing threats to information processed, stored, and transported by internetworked information systems.” (Reference 1)
Today’s cybersecurity focuses on reducing the attack surface outside the traditional solutions like firewalls, network segmentation, and or system controls.
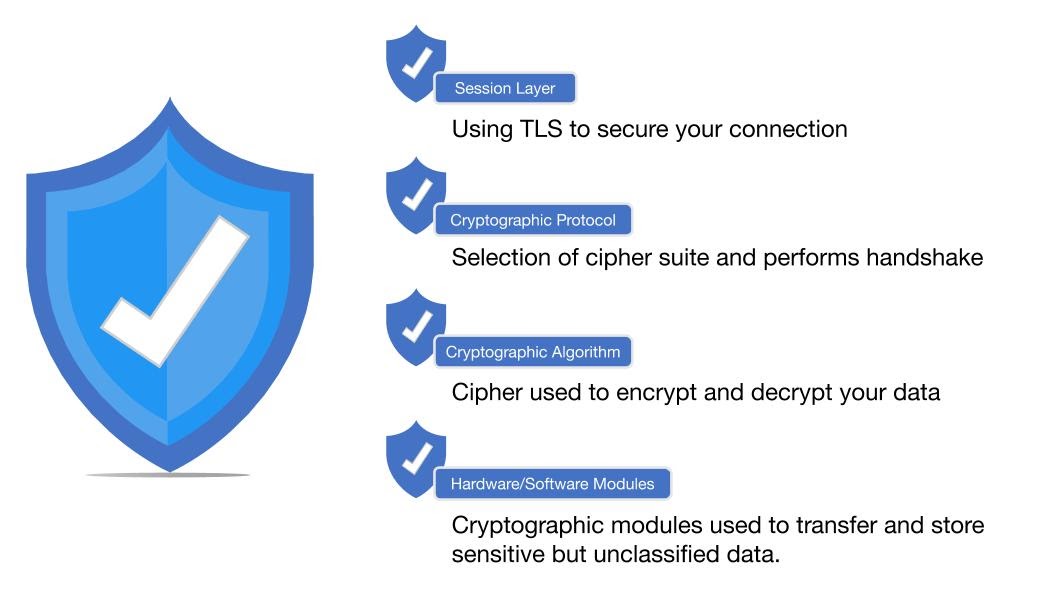
Whether in-transit or at-rest, your data is vulnerable to attacks from hackers and other malicious actors. That’s why protocols like Transport Layer Security (TLS) are used to help to secure data point to point with data encryption, which converts plaintext into ciphertext using both hardware and software modules.
The TLS protocol supports the use of numerous cryptographic protocols. Knowing how to use and or configure these protocols can be difficult if not near impossible to understand, but this knowledge is key to providing the level of security required to thwart attacks.
In order to establish a secure connection, the protocol requires the selection of a cipher-suite and key to encrypt your data. The NIST Cryptographic Module Validation Program (CMVP) provides instructions on conformance testing of cryptographic modules. The assessment covers eleven areas with regards to the design and implementation of a cryptographic module, to ensure the overall rating meets your requirements.
Using vulnerable cryptographic modules or ciphers can lead to attacks such as bypassing the seeding process used to generate keys leaving you vulnerable to attacks, which is why rigorous testing and certification is so important.
What FIPS Is and How It Addresses Security
The Federal Government requires all hardware and software components it uses to meet Federal Information Processing Standards (FIPS) 140-2, titled “Security Requirements for Cryptographic Modules.” This standard is applicable to all Federal agencies that use cryptographic-based security systems to protect sensitive information in computer and telecommunication systems (including voice systems), as defined in Section 5131 of the Information Technology Management Reform Act of 1996, Public Law 104-106. (Reference 2)
Implementations that comply with commonly accepted specifications provided by standards can save both time and money. Without standards to rely on, users may be required to become experts in every information technology (IT) product that is being considered for procurement. Also, without standards, products may not interoperate with different products purchased by other users. This could result in a significant waste of money or in the delay of implementing IT. (Reference 3)
Products can either be FIPS compliant or validated/certified. FIPS compliant is the weaker of the two monikers and simply means that part of the product has been FIPS validated. FIPS validation means that the entire product has gone through a rigorous certification process, conducted by NIST designated laboratories.
Konvoy, Kommander, Dispatch, and the entire line of D2iQ products have now received FIPS validation, the more stringent of the two standards. This process took months, but now that it is complete, government agencies can rest assured that their D2iQ Kubernetes Platform products and workloads have been certified secure by an independent laboratory following government standards.
D2iQ FIPS Validation
By obtaining FIPS validation, D2iQ eliminates your need to obtain domain-specific expertise in encryption protocols. We ensure that our infrastructure components automatically enforce encryption in-transit, vital to workload orchestration, and at the data layer for storage of sensitive data. D2iQ can operate in the Federal Government and in security-conscious industries such as healthcare and finance which demand proper use of protocols such as TLS and techniques like data-at-rest encryption all of which require the use of system cryptographic modules.
D2iQ worked with Acumen Security and just received FIPS validation of our products. This work ensures that the entire DKP stack uses D2iQ’s BoringCrypto, from certificate generation to mutual TLS. As a result, D2iQ’s DKP stack provides the “Day 2 Intelligence” in terms of security standards to use in sensitive environments such as government, finance, healthcare, or aerospace and defense.
D2iQ’s BoringCrypto library is key to protecting Sensitive But Unclassified (SBU) data. This library ensures your infrastructure meets or exceeds the guidelines for cryptographic algorithms and ciphers. The use of Federally approved cryptographic modules helps to reduce or eliminate vulnerabilities found in other Open-Source Software (OSS) libraries.
It is important to remember that FIPS doesn’t indicate there were no bugs or vulnerabilities in any products. For that process, D2iQ regularly patches our core components in a 2-week cycle and implements security vulnerability scanning in our continuous software development process. Please see our
blogs on release and patching the many components of the platforms for more information about this important topic.
FIPS validation, required by the Federal government for its own systems, is an important thing to look for in software systems that will manage sensitive data. By taking the extra step of obtaining FIPS validation of its products, D2iQ helps to boost your security posture, while reducing the load on your team.
References
1: ISACA, Cybersecurity Fundamentals Glossary, USA, 2016
2: What Is The Applicability Of CMVP To The US Government?, NIST FIPS-140.2 Instructions, 2020
3: FIPS 140, Security Requirements for Cryptographic Modules